Role-Based Access Control (RBAC)
Authorization refers to the role-based access control policies in that define what actions an authenticated entity may perform. In this system, permissions are specific actions, like running a query against a specific corpus, or resetting its contents. These permissions are grouped together into roles, and authenticated entites may be assigned one or more roles.
In this context, an authenticated entity refers to a user or an app client able to attest its identity by presenting a valid JWT token. Even entities that lack explicit roles may still be able to perform operations on the platform through the use of default permissions.
RBAC Roles
This section explains these concepts in further detail:
Account Level Roles
- Owner is initially granted to whoever created the account. It grants all the permissions of the admin roles, below, as well as the ability to delete the account.
- Account Administrators can perform all actions on a account, except managing billing activity. These actions include managing users, API keys, managing corpora etc.
- Corpus Administrators can perform all corpus related actions within the account. This includes authorizing user roles on an account, deleting a corpus, creating corpora, and transferring ownership of a corpus.
- Billing Administrators can view and edit account billing activity.
Corpus Level Roles
Users can also be authorized to perform various actions per corpus. You can assign roles in the Authorization tab on the Corpus page.
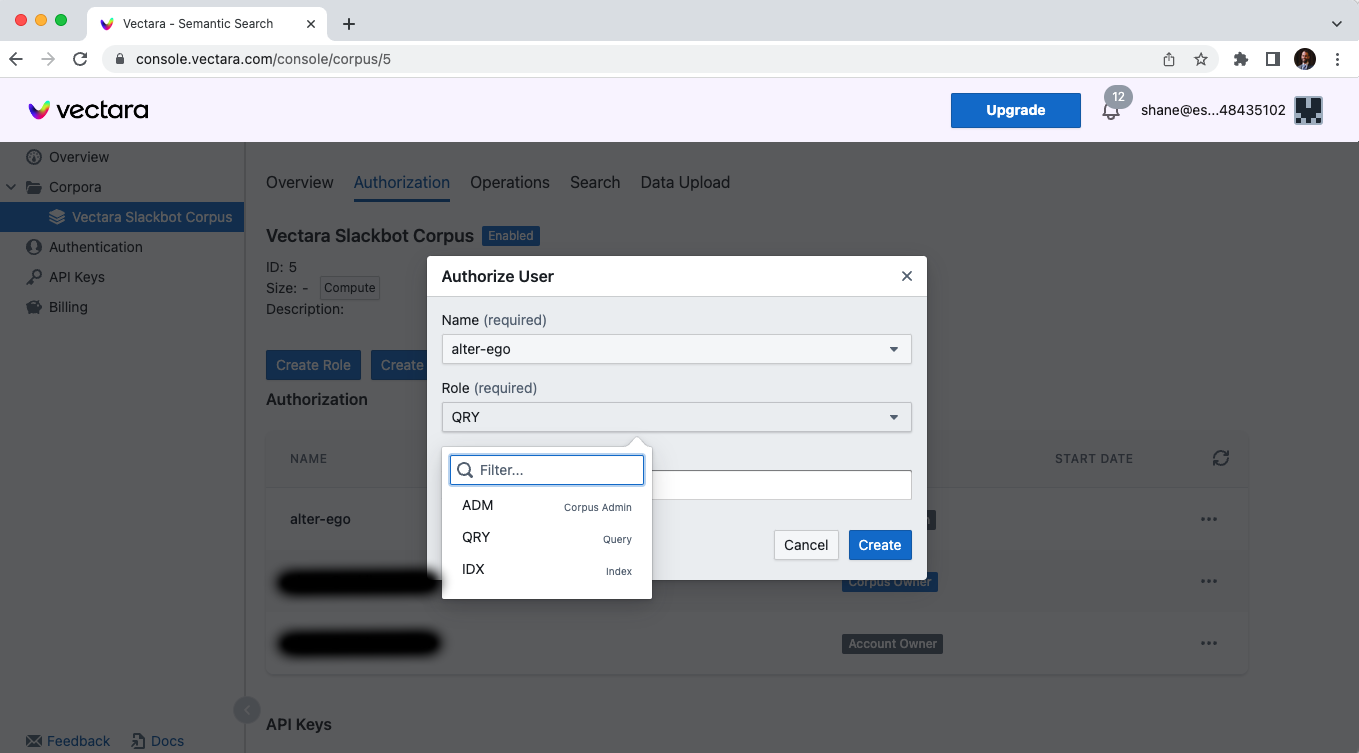
- The Query role (QRY) allows querying the corpus.
- The Indexing role (IDX) allows data to be added to the corpus.
- The Administrator role (ADM) allows query and indexing the corpus, but also resetting it, deleting it, adding and removing user access, and transferring its ownership.
A corpus may also specifying querying or indexing as default roles. A default role is a role that is granted to any authenticated user in the account. For example, if you want any authenticated user to be able to run queries on the corpus, you would add the query role as default.
Account Features
Account features differ from roles in that they are enforced for the entire account and are generally tied to account tier. These features include:
- Custom dimensions. Whether custom dimensions may be defined for corpora.
- Maximum corpora per query.
- Score retrieval. Whether or not downstream systems have access to the raw answer score. Advanced applications can utilize this information for thresholding, and for incorporation into downstream machine-learning systems.
- Encoder swapping. Whether the indexing and querying encoders be swapped to support semantic similarity matching in addition to question-answer matching.
- Textless. Defines whether corpora be built without storing the indexed text. Although all textual content is encrypted with per-corpus keys, this option may appeal when an even higher level of security is desired. Enabling this can potentially reduce the quality of search.
- User rate limit. Whether per-user rate limits can be defined.
- Corpus rate limit. Whether per-corpus rate limits can be defined.
- Corpus encryption key. Whether every corpus uses a separate encryption key for maximum security. Currently this feature is enabled for all accounts and cannot be disabled.
- Customer managed encryption key. Whether the account may use a customer managed master encryption key. This is an advanced feature that gives the customer total control over their data. By revoking access to the master key, the account will become inaccessible within minutes to the entire platform.
- Document metadata. Specifies whether document level metadata may be stored while indexing. This is currently enabled for all accounts.
- Document part metadata. Specifies whether part level metadata may be stored while indexing. This is currently enabled for all accounts.